#38690 [BC-Insight] A malicious coordinator can run multiple DKG coordination in parallel and manipu
Submitted on Jan 10th 2025 at 05:54:16 UTC by @ZoA for Attackathon | Stacks
Report ID: #38690
Report Type: Blockchain/DLT
Report severity: Insight
Target: https://github.com/stacks-network/sbtc/tree/immunefi_attackaton_0.9/signer
Impacts:
Network not being able to confirm new transactions (total network shutdown)
Description
Brief/Intro
DKG coordination is the crucial part of the system to generate aggregate key which is used for signing transactions. A coordinator can behave maliciously during their tenure by running multiple DKG coordination process in parallel and manipulate their order, which affects the entire network.
Vulnerability Details
The signers participate in DKG coordination rounds to share their public/private DKG shares, which at the end constructs an aggregate public key. When the DKG coordination round ends which is at the moment each signer receives DkgEnd message, signers store these aggregate keys into the database.
When signers are requested to sign a message, they trust the latest record of the database, thus using the latest aggregate key for signing messages.
So, thinking in the attacker's perspective, how can I break the signers network by letting signers have different perspective of "latest trusted aggregate key"?
To make this happen, one possible solution is for signers to participate in concurrent DKG coordination process which will result in different order of storing aggregate keys into the database. For example, signer-1 could store aggregate keys in the order of A, B, while signer-2 could store the keys in the order of B, A into the database.
Within current implementation of the protocol, it does not include a logic to prevent concurrent DKG coordination or the logic to settle concurrent DKG coordination correctly.
By abusing this implementation, a malicious coordinator can easily break the signers network by coordinating multiple DKG rounds at the same time. When the malicious coordinator distributes DkgEnd messages of multiple DKG rounds at the same time, there's high possibility of chances for signers to receive those messages in different order by the nature of the general network system.
Impact Details
The issue has crucial impact to the system since it will cause disagreements between signers that leads to halt of the entire system. And it's pretty easy for the malicious coordinator to execute this process.
References
sBTC codebase
Proof of Concept
Proof of Concept
The goal of the PoC is to demonstrate the discrepancy between signers regarding order of aggregate keys stored in the database. The PoC is tested on my local machine using provided dev environment with Docker.
To allow the coordinator to execute multiple DKG coordination, here's modified parts of the codebase:
In signer/src/main.rs, add more coordinators to simulate concurrent DKG coordination. In PoC, 4 concurrent DKG coordination is used as example.
For the coordinator process, txId of a DKG round is deterministic based on coordinator's public key and Bitcoin's chain tip. To allow concurrent coordination process, modify coordinator_id function in transaction_coordinator.rs to include some random information, as follows.
And for observation purpose, add a logging in transaction_signer.rs when DkgEnd is received, modification as follows:
Finally, to make the test easier, I modified bootstrap_signatures_required config in signer-config.toml to 3 which means all signers have to sign messages to make it valid.
With these changes, rebuild the signers binary and start the devenv using Docker. After waiting for minutes, there were no on-chain transactions happening as expected, while DKG coordination processes are finished and all signers have aggregate keys in their database.
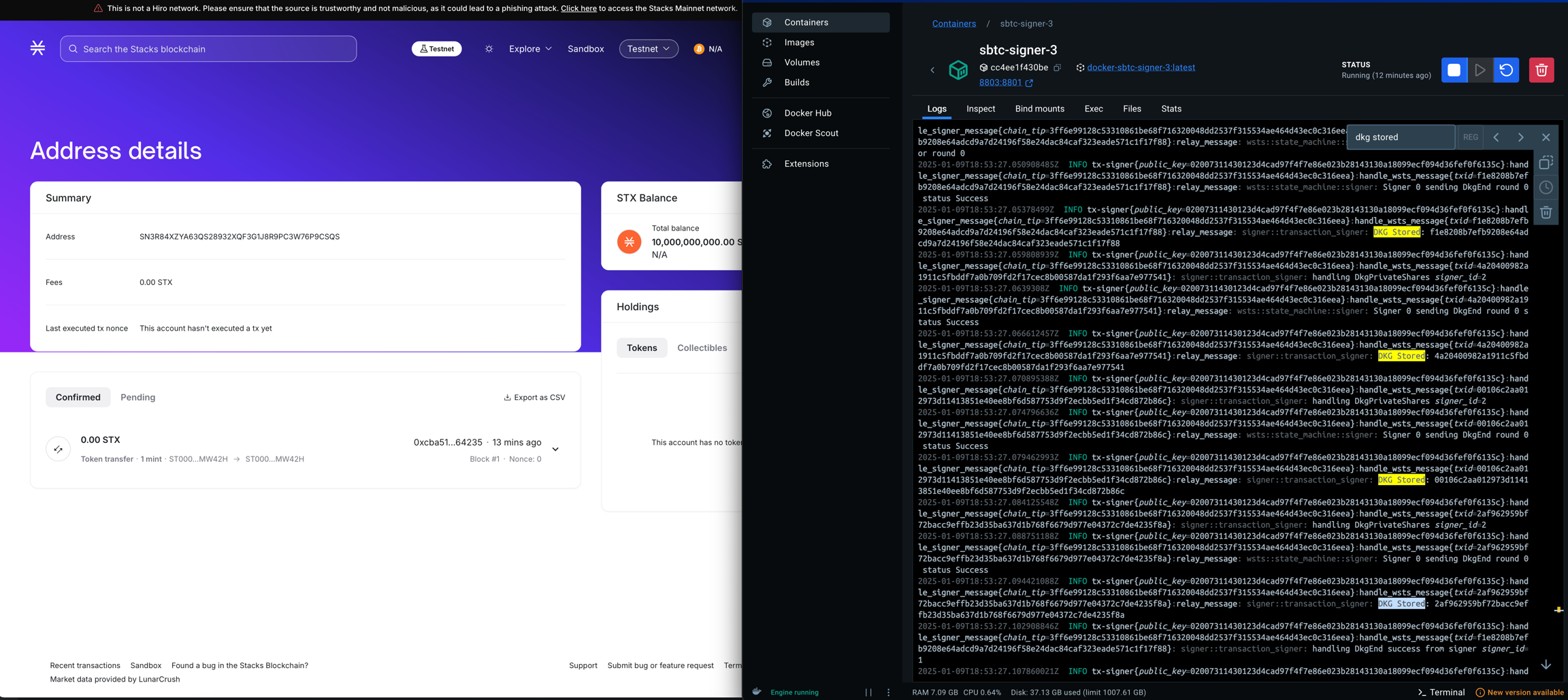
Here's some proof about the order of DKG coordination of each signer, and the latest aggregate key stored in each database.
sbtc-signer-1
sbtc-signer-2
sbtc-signer-3
As shown in the proof, signers have different order of DKG coordination processed, that results in discrepancy in order of storing keys in database.
Also, here's a screenshot as a proof that shows no transactions happening even after 12 minutes of system up and running.
Recommended mitigation steps
While txId of DKG coordination round is deterministic in perspective of the coordinator, integrity of txId is not checked by signers. As a simple mitigation, the signers should validate txId based on the coordinator's public key and Bitcoin's chain tip. This way, it can prevent concurrent coordination happening which is the root cause of the issue.
Last updated
Was this helpful?